From advanced phishing techniques to ransomware-as-a-service and the Log4J vulnerability, IT security threats are evolving and growing rapidly. For example, attacks on corporate networks grew by 50% from 2020 to 2021, according to Check Point Research1.
It now takes an army of experts using a complex, dizzying array of tools to defend the organization’s critical assets, which includes employees, data and systems:
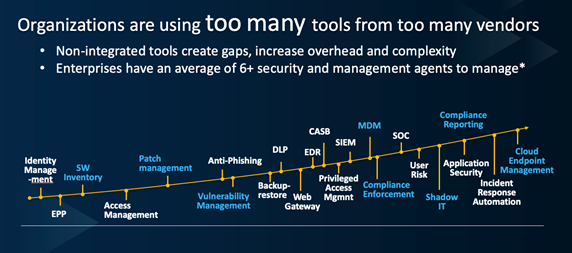
HCL
For this army to be effective in defending against onslaught after onslaught of cyberattacks, it must be coordinated. If the IT operations and security teams aren’t on the same page, working together to ensure security is embedded throughout the IT architecture, defenses will fail and breaches will occur.
Which of these 3 categories fits your organization?
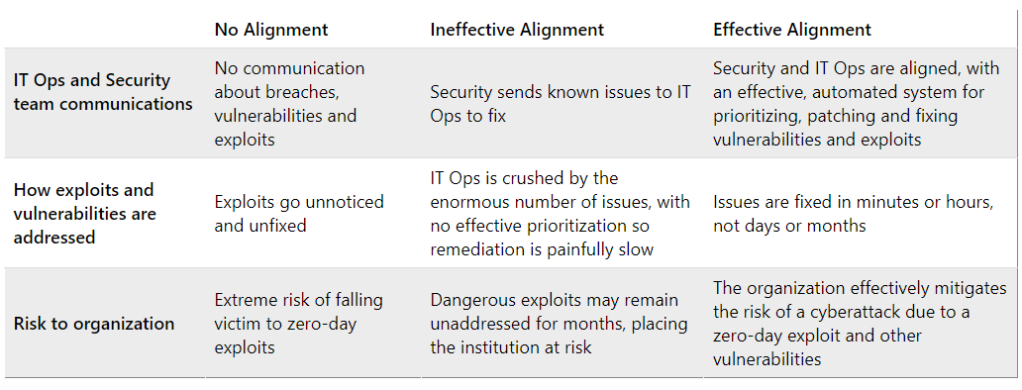
Enterprise IT and security teams tend to fall into one of three categories when it comes to IT operations and security unification. First, there are companies with teams that don’t talk to one another and frankly, have no real desire to do so. IT operations is focused on keeping systems running to minimize downtime, deploy new software, manage employee devices such as laptops, and other myriad critical tasks. Security is a concern, yet there’s little communication between IT operations and security about breaches, vulnerabilities, and other cybersecurity matters.
Three stages of IT Ops and Security Team Alignment
HCL
The results of this lack of alignment can be devastating. For example, the credit bureau Equifax failed to correct a known vulnerability in the Apache Struts website framework, even though a patch was available. Hackers exploited it and for two-and-a-half months were able to steal sensitive information on more than 180 million individuals. The company had to pay $575 million in fines, and both the CIO and chief security officer were replaced. The breach ultimately cost the company more than $2 billion.
Organizations that fall into the second category are working to bring IT Ops and security into alignment. However, the sheer scale of the information they share makes it difficult to prioritize work and shore up weaknesses in a timely manner. When a zero-day vulnerability emerges, hackers immediately begin work to exploit them, so the clock is ticking. Yet in many cases, IT operations receives spreadsheets from security with thousands of lines of software vulnerabilities, which require thousands of hours to interpret, find patches, and fix.
A Ponemon study2, for example, revealed that enterprise vulnerability scans uncovered just under 800,000 vulnerabilities and 28% of them were still not fixed six months later, leaving a backlog of more than 57,000 known vulnerabilities.
Finally, organizations in the third category have successfully unified IT operations and security, so that they work efficiently together to keep their company’s defenses strong. Typically, these are smaller enterprises without silos, and IT operations and security are often in the same functional unit. However, there’s no reason that larger organizations can’t share the same success.
Senior leadership across the organization must champion IT Ops and security unification, placing a priority on embedding security throughout the architecture. Success requires more than just will. Technology must also be employed to streamline and correlate what comes out of security’s vulnerability management tools so that IT operations can understand and prioritize the fixes that need to be made. Doing so can reduce the time-to-mitigate from days and weeks to minutes and hours.
Unifying IT operations and security, especially in large organizations, is no simple task. However with the right leadership and tech tools, enterprises can ensure that their defenses will hold.
Click here to discover how tools can help unify security and IT operations to lower risk and speed the remediation of vulnerabilities.
[2] https://www.ibm.com/downloads/cas/YLQPAJZV
Read More from This Article: Why It Takes a Coordinated Army to Remediate Vulnerabilities Fast
Source: News


