“Prepare for the worst.”
This is how Ukrainians got greeted when accessing the Ministry of Education website on the night of the 13-14 of January 2022. This was not the only Ukrainian website attacked: the Ukrainian Ministry of Foreign Affairs, Ministry of Education and Science, Ministry of Defense, the State Emergency Service, the website for the Cabinet of Ministers, and a few other official sites were also digitally vandalized.
The surprising nature of a website defacement attack is what makes it so powerful and scary. A message that might be detected and removed in a few minutes, sometimes hours, can have enormous political cost, and result in reputational damage and a loss of trust that takes time to recover. Of course, if the target is a business, there can also be an economic cost.
The Russian-Ukraine conflict displayed the most egregious defacement attacks
Defaced websites are difficult to find, as targets do what they can to conceal them from the public eye. However, in the case of the Ukrainian government, defaced websites were relayed by the press across the world which is exactly what the attackers intended to do.
In the above case, about 70 Ukrainian government websites were defaced and temporarily down in what was claimed to be the most significant attack on Ukraine in four years. The malware used to strike Ukrainian government websites has similarities to the NotPetya wiper. But, according to researchers, the defacement attacks on the Ukrainian had more capabilities “designed to inflict additional damage.”
Before the sites went offline, a defacement message appeared, warning Ukrainians to “prepare for the worst”. Access to most of the sites was restored within hours but the damage was done: it was covered significantly by the international media.
The Ukrainian government accused Russia of being behind the cyber-attack and alleged that the hack was in response to Russia’s failure in its talks with NATO over Ukraine. Experts at Ukraine’s information ministry published a timeline of how news of the attack spread, pointing out that Russian media reported it before Ukrainian outlets. Russia has not commented on the hack.
The attention-grabbing defacement attack on official websites was not the only consequence, the hackers also infected the computer systems of dozens of Ukrainian government agencies with destructive malware disguised as ransomware.
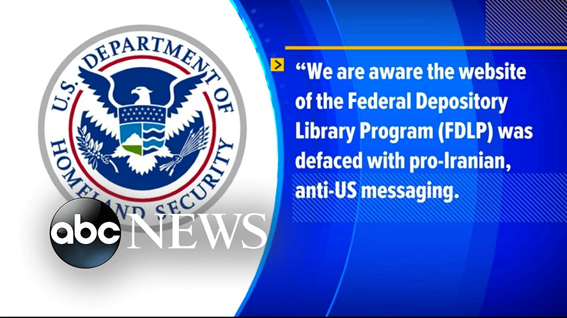
US Library Program Website 2020 defacement by Iranian hackers
ABC News
Another attack that generated significant media attention occurred in the US in January 2020. The hack happened two days after a top Iranian general was killed. The US government site, operated by the Federal Depository Library Program, was defaced by Iranian hackers claiming to represent the government of Iran.
The defacement message featured a disturbing image of former President Donald Trump with a vengeful note: “Hacked by Iran Cyber Security Group Hackers. This is only small part of Iran’s cyber ability! We’re always ready.”
The damage provoked by this attack was more symbolic than destructive. The fact that the hacked site was created to provide public access to Federal Government information, combined with the shocking message, attracted many media outlets.
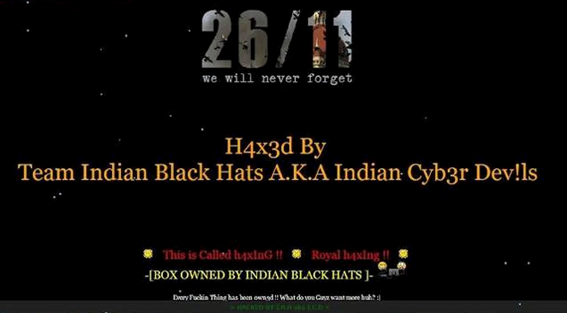
26/11 We will never forget defacement attack against Pakistan
screenshot of defaced message on www.fu.edu.pk
A group of Indian hackers, called “Indian Black Hats” launched a symbolic cyber-attack against Pakistan in revenge for the 26/11 Mumbai attacks. They hacked into two government sites and around ten non-government domains on the fourth anniversary of the terror attacks.
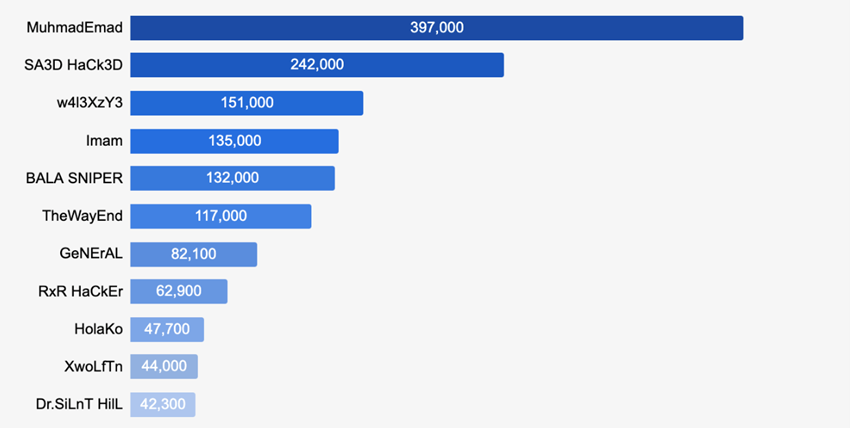
Rapid growth in the number of defacement attacks
The data below shows who are the most active hackers based on the results of a research conducted by Wordfence. The graphic represents the number of pages defaced by hacking campaigns. According to Wordfence, as indexed by Google, the total number of defaced pages for all the researched campaigns increased by 26% in just 24 hours.
Wordfence
Anatomy of defacement attacks
Homepages are the most affected pages in website defacement attacks. But in some cases, internal pages are also defaced, or even the entire site is made non-functional by hackers. Although some attacks do not go beyond the change in how a website looks, some others represent a more serious security breach and the leak of sensitive data.
Hackers almost always use high-impact images with a black background. The visuals normally represent the reason behind the attack. And the perpetrator is generally mentioned within the image but not as text.

Visualping
How is your website defaced?
Hackers use automated scanning software to find vulnerabilities in the security system. And they take advantage of a break in the program to access the website. To deface websites, hackers use different methods. A common way is including infected code into the site’s script through an update. This allows them to take control of the website and gain access to its content.
Hackers also get access to passwords using phishing techniques where they pretend to be legitimate entities like friends, family, colleagues, or a company and send a link via email or text. When the victim clicks on the malicious link, it downloads malware that steals the password details. In other cases, these links lead to a form to fill in with personal information.
Defacement monitoring
Using the website defacement tracking tool Visualping, you can monitor your business website and get a real-time alert as soon as an attacker compromises your system. You will know before any of your customers do, so you will be able to react fast and minimize the damage.
This is how it works: you introduce the URL you want to track and create your account with Visualping. The system takes screenshots from a third-party server and compares them to a previous screenshot. The external service inspects the site just as any visitor would. So, when it crawls the page and detects new content, it triggers a notification. Visualping also allows you to disregard dynamic content like videos, ads, or sliders to avoid false alerts.
Depending on the importance of the page, users can choose different frequencies of checks. Home pages, for instance, should be checked every 5 min to detect defacement attacks, whereas deeper pages might be checked every hour or less frequently.
What to do if your website is defaced?
If you website is defaced, you may want to follow these steps:
- If you have a vendor-hosted website, contact them to report the anomaly.
- Replace the affected pages with a maintenance page as soon as possible.
- Inspect the latest back-ups looking for vulnerabilities and hidden malware.
- Restore your website with back-ups to ensure quick recovery.
- Inform your customers, suppliers and third parties about the incident.
- Make a public statement to preserve your organization’s reputation.
- Report the incident to the police.
- Analyze how the website was defaced and evaluate the response to improve for future complications.
How to secure your website
To help protect your website from defacement, you may consider these security tips:
- Use strong passwords and avoid default log-in credentials.
- Manage the access for user accounts and keep it updated.
- Always have a back-up to respond to an incident.
- Train your employees on how to respond to incidents.
- Use a firewall to block malicious users.
- Use change detection tools to identify unauthorized changes.
- Backup your database regularly and before performing updates.
- Update plug-ins to fix bugs and patch security issues.
- Install updates and patches on your website server.
There is no such thing as perfect security. Even some of the world’s biggest websites have been hit by defacement attacks at some point. So, in the event that a hacker does deface your website, you will need to have a security action plan to get it fixed as fast as possible.
There are simple services, such as Visualping, that alerts companies when their website is defaced. More coverage on this subject on Defacement monitoring: deceptively simple defense against hackers.
Read More from This Article: Website Defacement: Petty Cyber Attack…Big Consequences
Source: News


