Cybersecurity is at an inflection point. The move to remote working and the endpoint vulnerabilities that go with it are a permanent part of the new normal.
There are multiple factors causing organizations to rethink their security strategies. For example, ransomware is now a successful business model for a new breed of smart, deep-pocketed bad actors. Also, it is difficult and costly to find and retain cybersecurity professionals with the expertise to protect enterprise data against a new generation of attacks. In addition, most enterprises use multiple tools and solutions that must be managed by lean, in-house security teams.
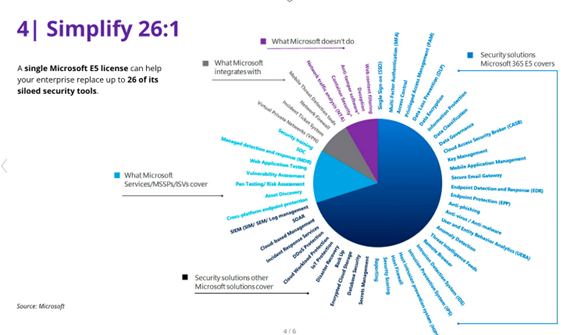
First: Simplify
The first step in dealing with any overwhelming situation is to make it simpler.
Organizations don’t need to deal with multiple different vendors and tools, each with different license agreements and upgrade cycles that require integration with each other. Reducing their number should be at the top of your to-do list.
One approach is to adopt an integrated suite of security products from a single vendor. For example, most organizations already use Microsoft 365, which includes Microsoft Teams and other Microsoft applications. Also, many of these customers have purchased the E5 security suite, which includes Microsoft’s integrated security features that protect Microsoft 365, endpoints, and cloud applications, as well as providing identity and compliance management.
“Microsoft has market-leading security products and tremendous scale to back them up,” said Peter Scott, Director of Security at DXC Technology. “In addition, Microsoft is investing $20 billion in security over the next five years. Considering this investment and dedication to security, it makes sense for organizations to consider Microsoft when looking to simplify their security toolsets.”
The degree to which you can consolidate may be surprising. It’s possible to consolidate 26 separate tools onto Microsoft and its partners:
Microsoft
Perceptions are changing
Analysts that evaluate cybersecurity software, such as Forrester Research and Gartner, increasingly rank Microsoft security products among the leaders. One reason is the vast amount of worldwide security signals that Microsoft gathers – valuable intelligence that the company is leveraging to build highly effective software to defeat the bad actors.
“Microsoft has a very large, cyber Petri dish within which to research cyber threats,” said Scott. So, when large-scale attacks occur, Microsoft has the cyber intelligence that is instrumental in taking down the bad guys.”
For example, Microsoft cybersecurity tools map to the MITRE attack framework, and they are integrated with each other. This integration capability reduces the burden on your cybersecurity teams and it can help to better protect the enterprise by preventing malware from moving laterally within an organization.
However, Microsoft Security goes beyond securing Microsoft products. It also now helps protect AWS and Google Cloud environments, as well as Linux, MacOS, iOS for iPhone, iPadOS, and Android.
Another advantage: From the Microsoft Sentinel security information and event management (SIEM) solution, you can view your entire cybersecurity environment from a single pane of glass. Having this visibility delivers confidence that security tools and policies are working as they should.
How to implement Microsoft cybersecurity
What next? As an enterprise, you may not be ready to rip out your existing defenses and install new ones. That would be a risky maneuver that would be hard to justify. Instead, plan a security journey to replace point products as you leverage the Microsoft suite. At every step, test integrations with your existing environment, and ensure that effective monitoring and protections are working.
Being part of the large Microsoft ecosystem brings with it the benefit of extensive real-time information sharing, Scott said. For example, as a customer, when you send threat information to Microsoft, that anonymized data is pooled with input from Microsoft’s other customers in a process similar to crowdsourcing. The data is then mined for insights that are returned to all enterprises, so everyone gains the benefit of shared experiences.
Getting started may feel daunting. That’s why it’s important to leverage an expert partner. DXC has decades of experience helping hundreds of the world’s largest enterprises to get the best value from Microsoft technology. As a global systems integrator, the company also has deep knowledge of third-party tools and how to integrate them.
For example, a large automaker turned to DXC for help with Azure Sentinel and Azure Defender for IoT — moving from stove-piped, multi-tooling solutions to a unified security service with enterprise-wide protection.
DXC also supported a global manufacturing leader in the implementation of Microsoft Sentinel, which has transformed an environment with multiple disparate tools into a unified, well-monitored cybersecurity service. Also, because the manufacturer operates with more than 40,000 onsite and offsite users, the company benefitted from DXC’s global partnership with Microsoft and expertise in maximizing the value of Microsoft Office 365 E5 licensing with its advanced security capabilities.
“Sometimes security is bolted on afterwards,” Scott said. “That’s not how we think of security at DXC. Security needs to be embedded in the operational environment.”
With more than 3,000 cybersecurity professionals worldwide based in regional centers of excellence, DXC can protect data effectively, economically, and locally.
“DXC runs IT for some of the largest and most complex companies in the world every minute of every day,” said Scott. “That gives us visibility and experience that’s unrivaled, and it positions us really well to help our customers remain secure.”
Click here to discover more about the DXC and Microsoft partnership.
Cyberattacks, IT Leadership
Read More from This Article: Simplifying Security for the Hybrid Working World
Source: News


