“Prepare for the worst.”
This is how Ukrainians got greeted when accessing the Ministry of Education website in January 2022. It was not only this site impacted but, shockingly, the Ukrainian Ministry of Foreign Affairs, Ministry of Education and Science, Ministry of Defense, the State Emergency Service, the website for the Cabinet of Ministers, and other official sites.
The digital vandalism lasted a few hours, with many visitors and the press discovering the attacks. Screenshots circulating across the internet. The attackers getting free press. Total disaster.
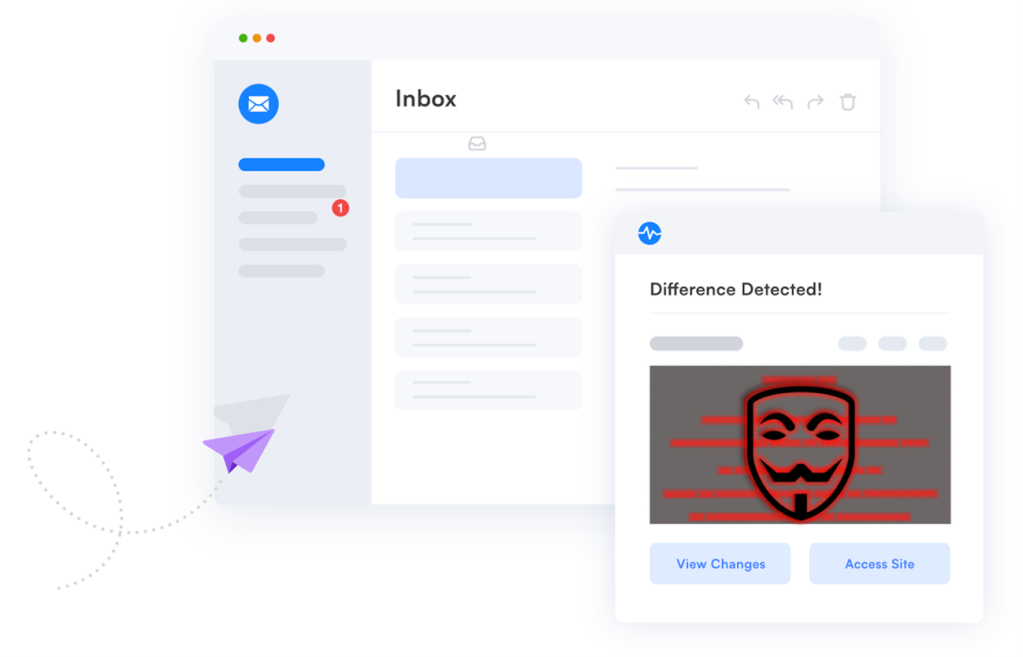
Defacement monitoring, on the other hand, allows website owners to be alerted if their site has been attacked in record time—before visitors realize it.
Hackers will spend countless hours trying to penetrate your website and can eventually manage to do it in spite of all defenses. Monitoring is a sure-fire way to limit the impact of website defacement.
What is website defacement?
Defacing a website means changing its appearance with no authority to do so. In most website defacement attacks; hackers insert inappropriate and malicious images on the homepage. But in some cases, internal pages are also affected, or they even make the entire site non-functional.
Having website defacement monitoring tools in place is decisive to detect these attacks and react accordingly.
Consequences of a defacement attack
When defacing a website, hackers’ intentions are not always about making money. Unlike other cyberattacks, defacement is often carried out by hacktivists who often deface a website just to take some revenge, prove their point, humiliate a government or organization, or disrupt a website’s operations.
Whatever the hackers’ intentions are, a website defacement attack is always problematic for an organization. It needs to be identified and fixed quickly to minimize its consequences.
Website defacement may be able to be removed within a few hours, but it will have an enormous economic cost and legal consequences in the long run. Worst of all, the reputational damage caused will be very challenging to repair. If individuals see your defaced website, they will be less likely to trust your company and to give their personal or payment details in the future.
As such, it is essential to take all the necessary steps to make your security defenses robust, detect vulnerabilities before a hacker does and have a plan of action in case a group of hackers manages to breach the system.
Defacement monitoring tool
As these attacks become more frequent, website defacement monitoring tools are useful for IT security teams and site owners to detect the changes as soon as they happen. Visualping is a simple to use tool that complements your IT security software to keep your business website at guard.
With Visualping, you can track unauthorized changes on webpages or entire sites and get real-time alerts when a visual or code change occurs.
You just introduce the URL you want to track and create your account with Visualping. The system takes screenshots from a third-party server and compares them to a previous screenshot. The external service inspects the site just as any visitor would. So, when it crawls the page and detects new content, it triggers a notification. Visualping also allows you to disregard dynamic content like videos, ads, or sliders to avoid false alerts.
One of the most popular features is the ability to disregard dynamic or moving parts of the pages like videos, banners, or sliders. These can be blocked from the monitoring so that those receiving the alerts get notified only when relevant changes, authorized or not, occur.
Users can also opt for higher frequency monitoring through several subscription options. Depending on the importance of the page, you can choose different frequencies of checks. Home pages, for instance, are recommended to be checked every 5 min to detect defacement attacks, whereas deeper pages might be checked every hour or less frequently.
You will be notified of security breaches, and you can also monitor and keep evidence of accidental changes, DNS downtime, visual regres
You will be notified of security breaches, and you can also monitor and keep evidence of accidental changes, DNS downtime, visual regression and other changes in the code that are invisible to visitors.
Defacement monitoring or uptime monitoring?
Website uptime ensures that your website is constantly available to serve your customers. And uptime monitoring tools alert you when a page on your site is not loading successfully. This type of service is not useful when you are looking to detect website defacement attacks because they don´t monitor the look of the page.
When a website is defaced, it is still up and running while its content is modified. That’s why the right tool to identify that the content has gone wrong is one that visually compares the look of the page. And for that use, website change monitoring software are the right tools.
Conclusion
As perfect security is impossible, you should always be prepared to suffer a defacement attack. What will make a difference is having the right security reaction plan in place and knowing how to execute it. Tracking your most important website pages using a website defacement monitoring tool will give you great peace of mind. And in the unfortunate event of receiving an attack, it will be the starting point to execute the security response plan.
sion and other changes in the code that are invisible to visitors.
Defacement monitoring or uptime monitoring?
Website uptime ensures that your website is constantly available to serve your customers. And uptime monitoring tools alert you when a page on your site is not loading successfully. This type of service is not useful when you are looking to detect website defacement attacks because they don´t monitor the look of the page.
When a website is defaced, it is still up and running while its content is modified. That’s why the right tool to identify that the content has gone wrong is one that visually compares the look of the page. And for that use, website change monitoring software are the right tools.
Conclusion
As perfect security is impossible, you should always be prepared to suffer a defacement attack. What will make a difference is having the right security reaction plan in place and knowing how to execute it. Tracking your most important website pages using a website defacement monitoring tool will give you great peace of mind. And in the unfortunate event of receiving an attack, it will be the starting point to execute the security response plan.
Read More from This Article: Defacement Monitoring: Deceptively Simple Defense Against Hackers
Source: News